
Misconfigurations, inconsistent patching and incomplete control coverage remain some of the most common causes of compromise. The Essential Eight assessments and uplift provide a proven and prioritised set of mitigation strategies that help protect organisations from real attacks.
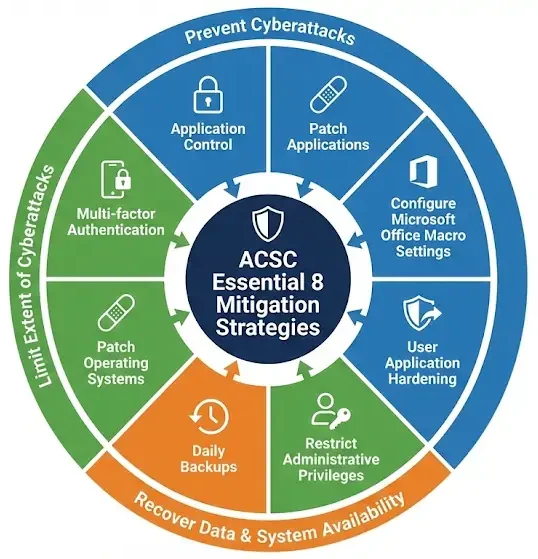
The Australian Signals Directorate (ASD) and Australian Cyber Security Centre (ACSC) Essential Eight gives organisations a measurable maturity scale that reflects how well their controls withstand increasingly capable adversaries.
dotSec performs independent Essential Eight maturity assessments across all four maturity levels. Our assessments identify how well your organisation meets the ASD maturity requirements, which risks remain and which improvements will deliver meaningful uplift.
dotSec will use the ASD/ACSC Essential Eight maturity model to assess your organisation against four maturity levels:
Our assessments identify how well your organisation meets the ASD maturity requirements, which risks remain and which improvements will deliver meaningful uplift.
This process will realise the following benefits for your business:
Some providers rely entirely on automated scanning, and market that output as an Essential Eight assessment.
Automated tools are useful but they cannot evaluate policy coverage, configuration consistency, privileged access designs, operating procedures or the subtle differences between intended controls and how they function in real environments. There’s an inherent risk in environments that have passed a scan, but which are later found to fail to correctly implement the guidelines, especially when evidence, procedures and configurations were reviewed.
A proper Essential Eight maturity assessment requires document analysis, interviews, observation, sampling and validation of control operation. That is the standard that dotSec applies.

Baseline Maturity Assessment (Levels Zero to Three)
dotSec begins with a structured, independent assessment of your current alignment with the ASD Essential Eight maturity model.
This includes evidence reviews, interviews, configuration sampling and technical analysis across selected systems, cloud services and user devices.
The objective is to determine your organisation’s maturity level for each of the eight mitigation strategies, from Level Zero through to Level Three. The assessment identifies where controls operate well, where they fall short of ASD expectations and where control design differs from actual operation.
Your baseline report provides a clear, factual and defensible view of current maturity that can be shared with IT, leadership and external stakeholders.

Control Effectiveness Verification
Once the baseline is established, dotSec verifies how effectively the in-scope controls operate day to day. This includes reviewing configuration consistency, analysing operational processes, checking evidence of repeatability, and validating that implemented controls genuinely meet the intent of ASD’s maturity level requirements.
This step highlights the difference between “controls exist on paper” and “controls operate as designed”. It also identifies systemic issues such as configuration drift, dependency on manual workarounds or gaps that automated scanning tools simply cannot detect.
Your verification report provides practical insights into which controls deliver real protection and which require redesign or improvement to reach higher maturity levels.

Targeted Uplift Roadmap and Implementation Support
dotSec delivers a prioritised and actionable improvement roadmap that aligns with ASD’s maturity model, your operational constraints and your risk profile. Recommendations are structured to support rapid uplift where it has the greatest effect and strategic changes where deeper improvements are required.
The roadmap outlines the steps needed to progress from current maturity to your desired maturity level. This can include improved patching cycles, configuration hardening, privileged access controls, application control policies, backup integrity processes and procedure updates.
dotSec can continue to assist by validating uplift progress, advising on control redesign and supporting ongoing improvement toward sustained Essential Eight maturity.
DotSec delivers Essential Eight assessment and uplift services that are practical, evidence driven and don’t just parrot the output of some scanning tool. We stand out for several reasons:
If you want an Essential Eight maturity assessment or support uplifting controls to higher maturity levels, dotSec can help.
Each engagement is tailored to your environment, your risks and your operational goals.
Contact us to schedule a discovery discussion and begin your Essential Eight uplift.
Practical and experienced Australian ISO 27001 and ISMS consulting services. We will help you to establish, implement and maintain an effective information security management system (ISMS).
DotSec’s penetration tests are conducted by experienced, Australian testers who understand real-world attacks and secure-system development. Clear, actionable recommendations, every time.
dotSec stands out among other PCI DSS companies in Australia: We are not only a PCI QSA company, we are a PCI DSS-compliant service provider so we have first-hand compliance experience.
Web Application Firewalls (WAFs) are critical for protecting web applications and services, by inspecting and filtering out malicious requests before they reach your web servers
Multi-Factor Authentication (MFA) and Single Sign-On (SSO) reduce password risks, simplify access, letting verified and authorised users reach sensitive systems, services and apps.
dotSec provides comprehensive vulnerability management services. And we analyse findings in the context of your specific environment, priorities and threat landscape.
We don’t just test whether users will click a suspicious link — we also run exercises, simulating phishing attacks that are capable of bypassing multi-factor authentication (MFA) protections.
DotSec’s penetration testing services help you identify and reduce technical security risks across your applications, cloud services and internal networks. Clear, actionable recommendations, every time!
dotSec has provided Australian managed SOC, SIEM and EDR services for 15 years. PCI DSS-compliant and ISO 27001-certified. Advanced log analytics, threat detection and expert investigation services.
We provide prioritised, practical guidance on how to implement secure configurations properly. Choose from automated deployment via Intune for Windows, Ansible for Linux or Cloud Formation for AWS.
Secure web hosting is fundamental to protecting online assets and customer data. We have over a decade of AWS experience providing highly secure, scalable, and reliable cloud infrastructure.
DotSec helps organisations to benefit from the ACSC Essential Eight by assessing maturity levels, applying practical security controls, assessing compliance, and improving resilience against attacks.
We have over 25 years of cyber security experience, providing practical risk-based guidance, advisory and CISO services to a wide range of public and private organisations across Australia.















