
It was the great Gordon Ramsay that said, “I don’t like looking back. I’m always constantly looking forward. I’m not the one to sort of sit and cry over spilt milk. I’m too busy looking for the next cow.” But still, it can’t hurt to keep track of how the cow-hunting is going, so in this post, we’ll present some penetration testing stats from the past two years, and we’ll see if we can glean some insights and perspectives.
Penetration testing (also known as “pen testing”) involves a trained expert searching for vulnerabilities in a computer system which could be exploited by an attacker. There are many types of pen tests that focus on many kinds of targets, such as:
There are two benefits to pen testing. Firstly, pen tests allow you, our client, to identify and remediate vulnerabilities in your systems in an ethical, safe way by running what is effectively a controlled cyber attack that (unlike the real thing!) won’t leave you high and dry.
The second, almost secondary benefit of performing regular pen tests is that our client’s can check that their organisation’s security systems are equipped to handle the effects of an attack if one was to take place. Some might say that including an incident-detection and response (IDR) component into the exercise makes it more like a red-teaming event. Red-teaming however brings with it many other considerations, and Dotsec believes it is important to include an element of IDR when pen testing our client’s systems, to help them be ready to detect any attackers that later come their way!
At Dotsec, our pentesting process is both effective and client-centric. The process includes the following steps:
What’s to show for all of this? A client who can sleep more easily knowing that they have been able to identify, understand and remediate the vulnerabilities in their systems.
So, on to our review, which we’ve neatly summarised in just three graphs.
At DotSec, we perform a lot of pen tests. We collected data about the last 2 years of pen tests we’ve done and looked for interesting trends in the number of tests, industry types of our clients, and the size of their organisation.
The graph below shows the number of pen tests conducted from Q3 2020 to Q3 2022. We’ve seen an increase of approximately three times the number of pen tests in that time period. We believe this is a result of several things:
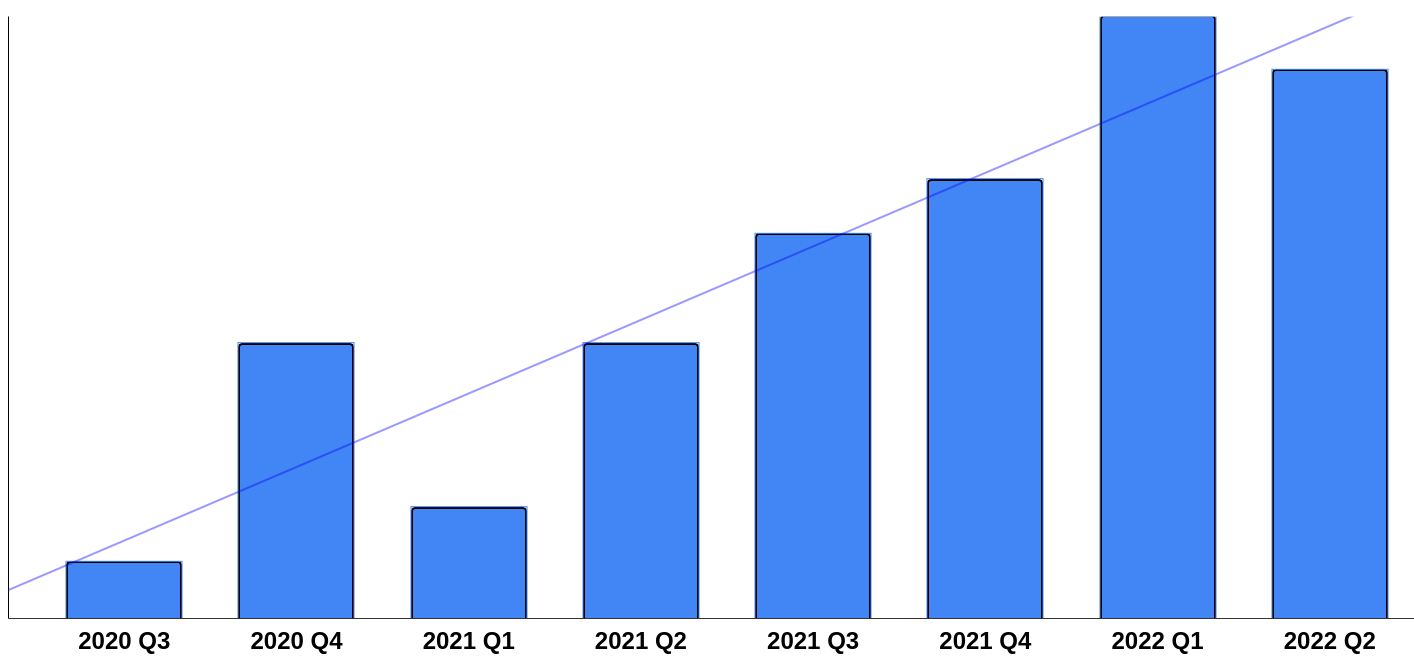
And don’t forget that we’re only three quarters through 2022, so it looks like the trend is continuing.
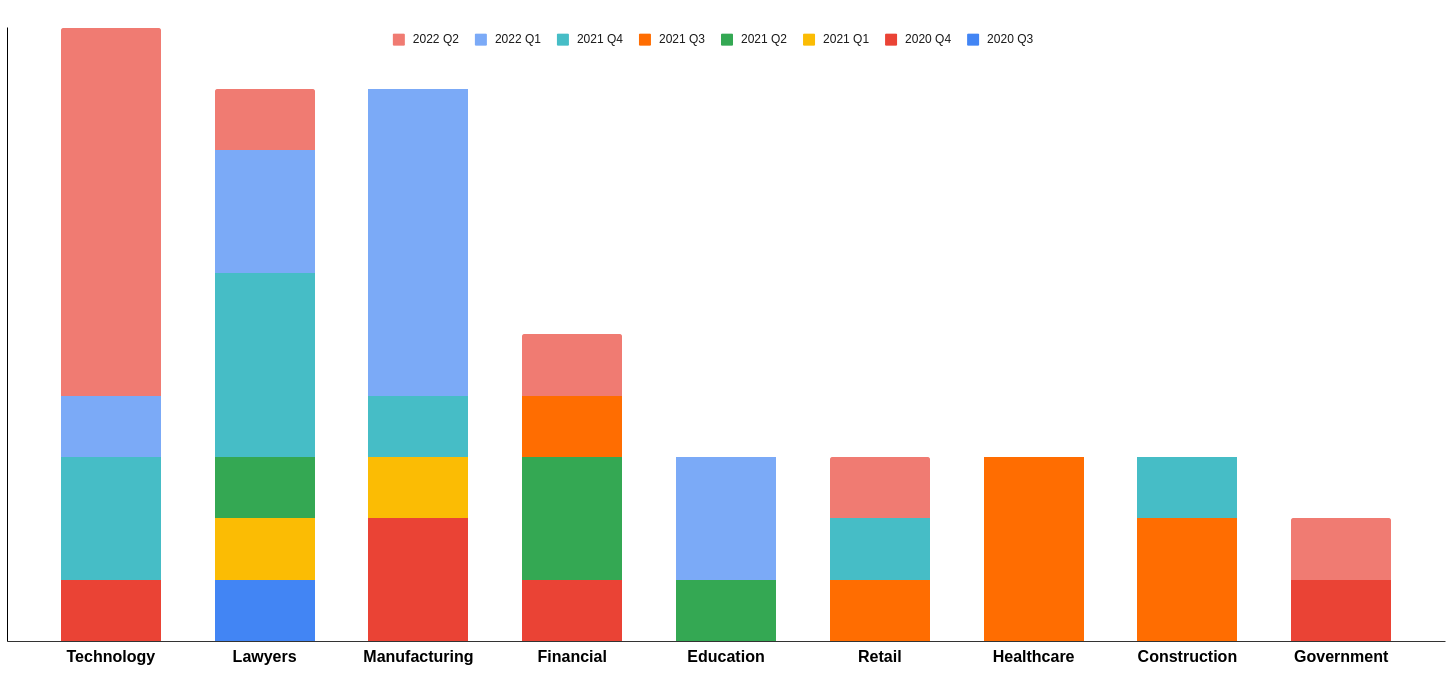
We also thought it would be interesting to compare which industry types appeared to be more interested in pen testing. We thought about this a fair bit and while we’re a bit concerned that our sample size isn’t large enough to make any concrete statements, but we were able to observe that:
The industry types who are performing regular pen tests appear to correlate to the increased requirements for security. For example, law firms are commonly being asked by their customers for attestations to show that regular pen testing is being done. Technology companies who are surrounded by IT news are well aware of the risks of not performing regular pen tests. We hope to get in touch with the industry types who haven’t contacted us about pen tests though!
What about the size of our clients? There are lots of theories out there: Are large organisations more likely to do pen testing because they have the budget? Or are small organisations more likely because there are less stages of approval slowing things down?
Actually, our data doesn’t support either theory! From our perspective:
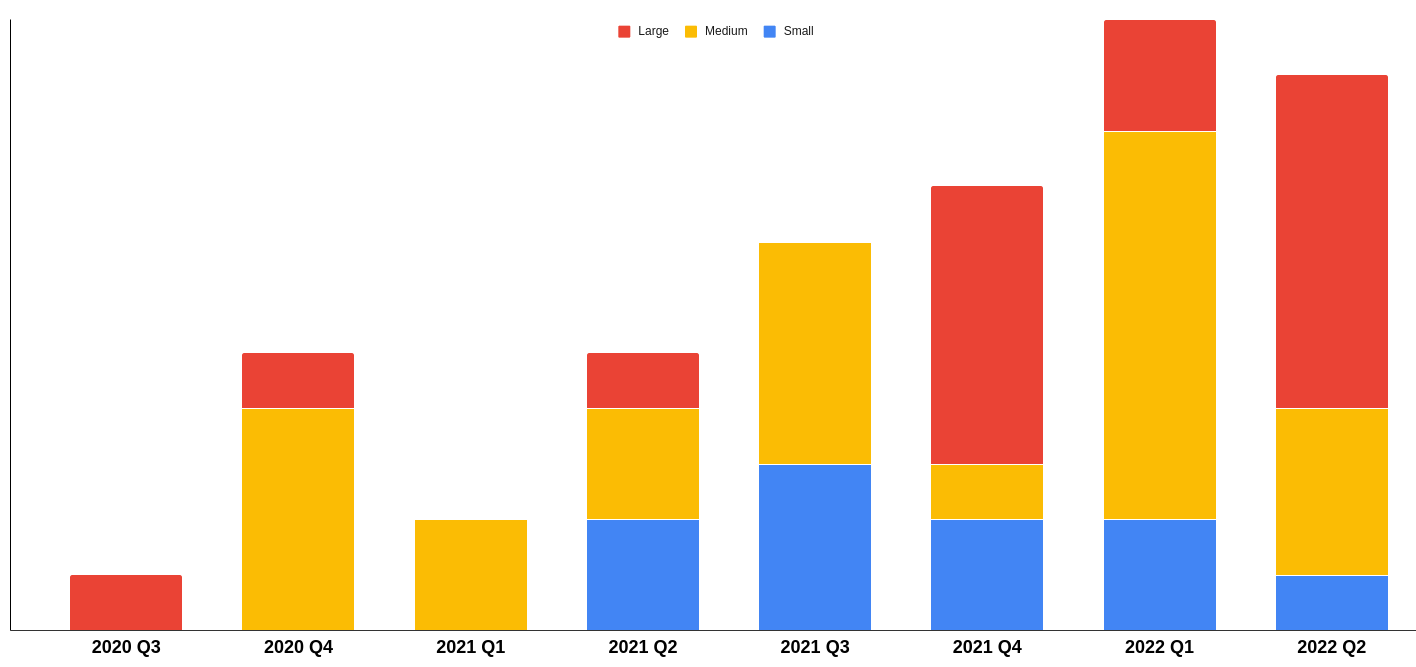
Of course, we all know the saying about the value of statistics…

But none the less, before we get back to our cow-hunting, what do we think we have learned from looking at our historical data?
So what should you consider?
If your organisation is part of an industry sector which is increasingly validating its security through penetration tests, but you have yet to join the party, consider the benefits that would be gained with increased confidence in your security controls and their ability to withstand attacks in today’s nefarious Internet.
On the other hand, if your organisation is part of a sector which typically eschews penetration testing and you consider it to be an unworthy expense, consider the advantages of overtaking your competitors with your proactive approach to security which is increasingly in the public’s eye given the number of breaches being publicised nowadays.
And finally, if you are in a sector without competitors (e.g. a government organisation) consider how grateful your customers (i.e. the tax/ratepayers) will be for protecting their PII by undertaking regular testing
Even if you regularly undertake penetration tests, consider rotating your testing provider: Just like a toothbrush which gets worn out scraping the same nooks and crannies in your teeth, sometimes changing your toothbrush will uncover new cavities.. and everyone enjoys a good filling!
In closing: We enjoy pen testing because we love helping our clients by identifying vulnerabilities in their systems, and then helping them to remediate the shortcomings. And our clients enjoy pen testing because they receive peace of mind that local experts (with lots of experience and no egotistical baggage) have tested their systems before the hackers do.