
We’ve all heard the saying: “You can lead a horse to water but you can’t make it drink”, right? Well, the Australian Securities and Investments Commission (ASIC) seems to have different ideas!
ASIC has commenced a law suit in the Federal Court of Australia. ASIC alleges [that] from March 2019 to 8 June 2023, FIIG Securities Limited failed to take the appropriate steps, as is required by an Australian Financial Services (AFS) licensee, to ensure it had adequate cyber risk management systems in place.
We’ve all heard the saying: “You can lead a horse to water but you can’t make it drink”, right? Well, the Australian Securities and Investments Commission (ASIC) seems to have different ideas!
ASIC has commenced a law suit in the Federal Court of Australia. ASIC alleges [that] from March 2019 to 8 June 2023, FIIG Securities Limited failed to take the appropriate steps, as is required by an Australian Financial Services (AFS) licensee, to ensure it had adequate cyber risk management systems in place.
The filing claims that FIIG was responsible for “systemic and prolonged cybersecurity failures” that allowed attackers from ALPHV to exfiltrate a claimed 385GB of data, in an attack that took place at FIIG in May 2023. ASIC’s federal court application is made under sections 1101B, 1317E and 1317G of the Corporations Act 2001 (Cth) (Corporations Act).
Furthermore, according to ASIC, “FIIG did not investigate and respond to the incident until 8 June 2023, almost a week after it had been notified of potential malicious activity by the ASD’s ACSC.”
Leaving ALPHV to play on your computers for six days is probably not going to end well, and ALPHV posted their ransom note on June 10:
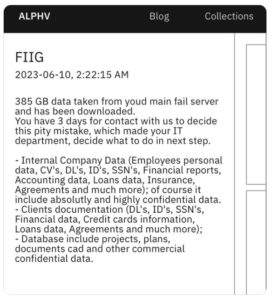
As you may remember, ALPHV was part way through it’s 2023 Across Australia tour at the time, having just returned from a gig where they exfiltrated roughly 4TB of data (about 2.2 million files) as part of their breach of the law firm HWL Ebsworth (that one is apparently being investigated by the OAIC) in April of that same year!
The ASIC application states in part, that in order to meet its obligations under s 912A(1)(d), FIIG was required to have available adequate financial, technological and human resources. ASIC further states that those resources were either not available and/or ineffective, and ASIC’s notice includes a list of “Missing Cybersecurity Measures”. The list runs across two pages (with an extra half page for “missing risk management measures”) and includes:
We’ve bleated on about all of these things in previous posts… risk-management, and control frameworks, and regular testing and assessment, and AOCs in previous posts…. and… oh for heaven’s sake, does no-one read our blog? 🙂
Two of the Missing Cybersecurity Measures that stood out for us were these:
As anyone who reads our posts (yes, both of you!) will know, we’re big on SIEM. How big? Welll…..
Yep, that big!
Why do we rabbit on about SIEM so much? Because it works and without it, you’re fighting blind! DotSec has been providing MSIEM services, assisting organizations across various industries in handling real-world cybersecurity incidents. In our next post, we’ll share a presentation that we used to highlight four case studies where we’ve used SIEM to help our clients with the following:
 ASIC is suing FIIG because “FIIG’s conduct exposed FIIG and its clients to the risk of a cyber intrusion and the adverse consequences thereof to a heightened and unreasonable extent”.
ASIC is suing FIIG because “FIIG’s conduct exposed FIIG and its clients to the risk of a cyber intrusion and the adverse consequences thereof to a heightened and unreasonable extent”.
ASIC Chair Joe Longo stated the obvious when said, “Cybersecurity isn’t a set and forget matter. All companies need to proactively and regularly check the adequacy of their cybersecurity measures.”
As business owners, one of our jobs is to manage business risks, especially risks to our clients and staff, as well as risks associated with business continuity and integrity.
And as we know, risks can be:
We have long suggested that it is better for a business to take the initiative and spend it’s hard-earned coin on it’s own terms, managing cost and risk as part of a mature security-control and risk-management framework. The alternative approach is to have the costs and payment plan dictated by one or more third parties, whether that be an attacker like ALPHV, and/or a regulator like ASIC.
As ASIC noted in the Concise Statement, “Had FIIG had the Missing Cybersecurity Measures in place, it would have detected suspicious activity on its network on or shortly after 19 May 2023, identified that its system had been compromised by on or about 23 May 2023, and prevented the threat actor from downloading some or all of the stolen data or, alternatively, had the opportunity to do so.”
So, what happens next? Well, ASIC fined RI Advice in 2022 for $750K plus the “costs of Security in Depth and the implementation of any Further Measures“, with the “engagement of Security in Depth referred to in paragraph 3(a) is to commence by no later than 1 month from the date of these Orders“. According to Allens, that was apparently the first time ASIC has exercised its powers in relation to cybersecurity risk management. Other commentators have suggested that ASIC’s action against RI Advice was a warning shot across the bow for other Australian businesses.
I have no idea if the RI Advice case is relevant to or sets a precedent for the FIIG proceedings. But if we look at the scale of the RI Advice and FIIG breaches, we see that although RI Advice suffered nine breaches over seven years, the broadest impact was described as “the potential compromise of Personal Information of several thousand clients and other persons“. “Several thousand” contrasts sharply with ASIC’s allegegation that FIIG’s failings “enabled the theft of approximately 385GB of confidential data, with some 18,000 clients notified that their personal information may have been compromised“. Time will tell on that one, but the initiative does now seem to be with ASIC and the Federal Court.
As Robert S. Mueller, III, former Director of the FBI and Special Counsel into the Russian interference of the USA election noted: “There are only two types of companies: Those that have been hacked and those that will be hacked.” But Mueller’s advice was not given so that we could all just throw our hands up in the air and give ourselves over to abject, pre-ordained hopelessness like Marvin.
Meuller’s advice was in fact optimistic: It is reasonable, prudent and cost-effective to manage risk pro-actively, and to maintain a suitable level of cyber security maturity; that way, when an attack does come, there is a realistic expectation of timely detection, investigation, defence and recovery, without major consequences for the organisation’s client base.
Mueller’s advice was not only optimistic, it was also amazingly prescient in light of HWLE, RI Advice, Optus, Medibank, FIIG and so many other breaches. Why? Because Mueller made his observation in 2012!
Give us a call! We really can help with all of this and we have 25 years of references to back us up. We look forward to hearing from you soon.
Practical and experienced Australian ISO 27001 and ISMS consulting services. We will help you to establish, implement and maintain an effective information security management system (ISMS).
DotSec’s penetration tests are conducted by experienced, Australian testers who understand real-world attacks and secure-system development. Clear, actionable recommendations, every time.
dotSec stands out among other PCI DSS companies in Australia: We are not only a PCI QSA company, we are a PCI DSS-compliant service provider so we have first-hand compliance experience.
Web Application Firewalls (WAFs) are critical for protecting web applications and services, by inspecting and filtering out malicious requests before they reach your web servers
Multi-Factor Authentication (MFA) and Single Sign-On (SSO) reduce password risks, simplify access, letting verified and authorised users reach sensitive systems, services and apps.
dotSec provides comprehensive vulnerability management services. And we analyse findings in the context of your specific environment, priorities and threat landscape.
We don’t just test whether users will click a suspicious link — we also run exercises, simulating phishing attacks that are capable of bypassing multi-factor authentication (MFA) protections.
DotSec’s penetration testing services help you identify and reduce technical security risks across your applications, cloud services and internal networks. Clear, actionable recommendations, every time!
dotSec has provided Australian managed SOC, SIEM and EDR services for 15 years. PCI DSS-compliant and ISO 27001-certified. Advanced log analytics, threat detection and expert investigation services.
We provide prioritised, practical guidance on how to implement secure configurations properly. Choose from automated deployment via Intune for Windows, Ansible for Linux or Cloud Formation for AWS.
Secure web hosting is fundamental to protecting online assets and customer data. We have over a decade of AWS experience providing highly secure, scalable, and reliable cloud infrastructure.
DotSec helps organisations to benefit from the ACSC Essential Eight by assessing maturity levels, applying practical security controls, assessing compliance, and improving resilience against attacks.
We have over 25 years of cyber security experience, providing practical risk-based guidance, advisory and CISO services to a wide range of public and private organisations across Australia.















