The 2023 State of Cyber Maturity for Australian Law Firms survey invited legal professionals to share their approaches, motivations, decision making, and management towards cyber security.
DotSec commissioned independent market research firm Momentum Intelligence to conduct the survey in collaboration with Lawyers Weekly.
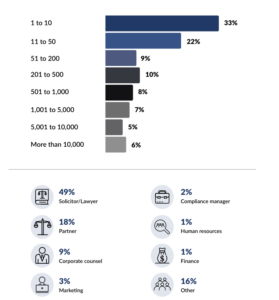
The survey was conducted on behalf of DotSec by Momentum Intelligence between 8 September and 4 October 2022. The survey received a total of 500 responses, including a total usable sample of 384 fully completed submissions.
The 2023 State of Cyber Maturity for Australian Law Firms report includes a range of findings which are grouped into three categories: Motivations (what makes the business push for better security), Maturity (how capable is the business when it comes to acting on their motivations), and Management (how do those that run the business govern organisational motivations and maturity).
Interestingly, the survey found that 48 per cent of Australian legal firms are confident in their ability to detect and respond to threats; the responses of these firms indicated a higher level of cyber maturity with processes and practices in place across the entire organisation. On the flip side however, the majority (51 per cent) of legal firms indicated that they are not confident in their threat detection and response capabilities.
Interestingly, the stats for these findings were being collected at around the same time as major Australian organisations Optus and Medibank have suffered significant data breaches. More recently, ASX-listed lender Latitude Financial suffered a major cyber-attack that saw somewhere around 300K customer identification documents stolen.
Respondents to this survey sometimes indicated that there were areas in which they might like to improve their organisation’s information security maturity, but that they were uncertain how to proceed in a cost-effective way. Here are some ideas (all of which are referenced in detail, in the report) to consider:

Cyber security is, in some ways, a rapidly evolving field, and many commentaries seem to be designed to achieve little more than hype up the FUD. It’s good for excitement, publicity and sales but doesn’t really help.
Firewalls, anti-malware, cloud, data-leakage prevention, endpoint protection, SIEM/SOAR/SOC… this list of cyber silver bullets is endless, and there’s always a new silver bullet to be sold. Yet evidence shows (more often now with the increasing number and severity of breaches) that sales-based cyber security doesn’t work, at least not for the customer.
Why? Because when products and services are sold without reference to a holistic, risk-based strategy, each product becomes just another solution looking for a stand-alone problem to address.
Of course, it doesn’t have to be so: Instead of a sales-focused approach, DotSec has delivered, holistic, customer-focused, risk-based cyber security services to legal firms (as well as most other industry sectors and all tiers of government) for 23 years. In fact, we started working with our oldest, ongoing legal client (a multinational firm) in 2002.
A customer-focused, risk-based approach to cyber security improvement requires a significant investment of our own time and resources, as well as a deep understanding of the customer’s specific needs and requirements. While such an approach might be seen as more challenging for the security provider, we have found the customer-focused, risk-based approach to cyber security to be ultimately more rewarding, both in terms of the financial and reputation benefits that it can bring to both parties.
So please, download the report, consider the above points, stand firm in the swirling panic, and set your own course. A well-mapped cyber security journey really can save your organisation time and money, and done right, can put you a cut above the rest.
We sincerely hope you enjoy the report and we look forward to any feedback you might have.