
How to undermine your pCI DSS compliance efforts
When it comes to PCI DSS compliance, most organisations focus on technical controls such as firewalls, encryption, and monitoring tools, to secure cardholder data.
However, even the most advanced technical safeguards can be rendered useless if employees mishandle cardholder data due to a lack of training.
Newer PCI DSS requirements focus on phishing and social engineering, which are increasingly being used to exploit human weaknesses in security. The clock stopped ticking back in March 31, 2025, so it’s well past the time to address the human component in your PCI DSS compliance success.
When it comes to PCI DSS compliance, most organisations focus on technical controls such as firewalls, encryption, and monitoring tools, to secure cardholder data. However, even the most advanced technical safeguards can be rendered useless if employees mishandle cardholder data due to a lack of training.
PCI DSS 4.0 has long included security awareness training as a best practice, but after March 31, 2025, new training requirements (12.6.2, 12.6.3.1, 12.6.3.2) become mandatory for all entities, depending on which Self Assessment Questionnaire (SAQ) they use. These new requirements focus on phishing and social engineering, which are increasingly being used to exploit human weaknesses in security.
Why employee training is critical for PCI DSS compliance
PCI DSS Self-Assessment Questionnaires (SAQs) are tools designed to help merchants and service providers assess their compliance with the Payment Card Industry Data Security Standard (PCI DSS). These questionnaires vary in complexity based on how a business processes, stores, or transmits cardholder data.
There are different SAQ types, such as SAQ A for fully outsourced e-commerce transactions, SAQ B for merchants using imprint machines or standalone dial-out terminals, SAQ C for businesses with payment application systems connected to the internet, and SAQ D for merchants or service providers handling significant volumes of cardholder data. Each SAQ consists of a set of security controls that must be implemented, along with an attestation of compliance (AOC) to confirm adherence.
Businesses use SAQs primarily when they are not required to undergo a full PCI DSS Report on Compliance (ROC) assessment, which is typically reserved for large enterprises processing high volumes of transactions. Small to mid-sized merchants, e-commerce businesses, and service providers completing SAQs do so to demonstrate compliance with PCI DSS requirements, reducing the risk of data breaches and avoiding penalties from payment brands. SAQs must be completed annually and are often required by acquiring banks or payment processors as evidence that businesses handling cardholder data are meeting security best practices. Failure to comply can lead to increased transaction fees, reputational damage, or even revocation of the entity’s merchant status.
Various PCI DSS requirements mandate that organisations provide formal security awareness training for in-scope employees upon hiring and annually thereafter. This training must be role-specific to ensure that employees understand the risks relevant to their job functions. For example:
- Finance and Accounting Staff must be trained on handling payment methods securely and be aware that cardholder data, including card numbers and PINs, must never be received via unapproved methods such as email.
- Developers must be trained on secure coding practices, ensuring that payment applications process cardholder data securely. They need to understand secure implementations of iframes and URL redirects instead of directly handling cardholder data and/or sensitive authentication data, if payment processing is outsourced to a third party service provider.
- Customer Service and Support Teams involved in payment processing need to recognise and report social engineering attempts where attackers try to manipulate them into disclosing cardholder data.
Despite these clear requirements, many organisations continue to under-invest in training, treating PCI DSS as an IT issue rather than an organization-wide responsibility. What could possibly go wrong?
What could possibly go wrong? A real-world example
Consider this real-world case: An accounting team, unaware (due to lack of training) of their PCI DSS compliance requirements, received card numbers and PINs via email from customers and stored them in a shared cloud storage solution for reference. The team was not acting irresponsibly, and they believed they were following efficient business processes. But in reality, because they had not been trained, their actions violated multiple PCI DSS requirements, including:
- Requirement 3: Protect stored cardholder data—Cardholder data was stored in email inboxes and shared storage without encryption.
- Requirement 4: Protect cardholder data with strong encryption during transmission—Card details were transmitted in plain text via email.
- Requirement 7 & 8: Implement strong access control measures—No strict access controls were applied to the cloud storage, leaving data exposed to unauthorised access.
Because of these violations, the company faced an urgent compliance audit, costly remediation efforts, and the risk of losing its ability to process card payments. This financial and reputational damage could have been avoided with proper employee training.
March 31, 2025 - The compliance hammer comes down!
Security awareness training has always been required for most SAQs. But when PCI DSS 4.0 came along, a number of new requirements were introduced as best practice, and because they were only best practice, they had no bearing on an entity’s compliance.
Alas, nothing good lasts forever, and so on March 31, 2025, three non-trivial requirements change and, rather than being just best practice, they will become mandatory:
- 12.6.2 – The training program must be reviewed at least annually and updated to address new threats and vulnerabilities that may affect the entity’s cardholder data and/or sensitive authentication data.
- 12.6.3.1 – Employees must be trained to detect and respond to phishing and social engineering attacks.
- 12.6.3.2 – Employees must be trained on the acceptable use of end-user technologies including explicit approval for use of technology and acceptable uses of the approved technology.
So what are the training-related requirements for the various SAQs? Here’s a table that summarises the March 25 before and after shots:
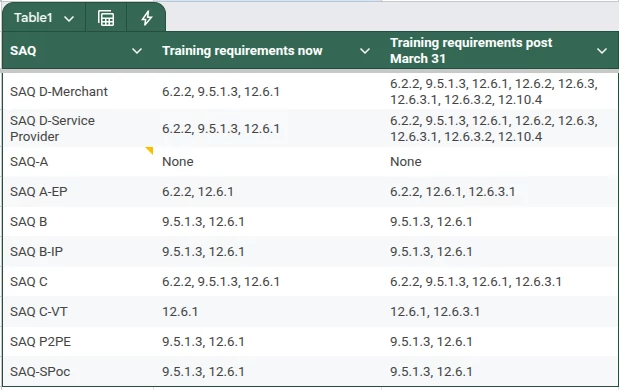
An analysis of PCI DSS SAQ training requirements shows that entities reporting under SAQ D (both merchants and service providers) will have the most comprehensive training obligations post-2025.
Only SAQ A gets a free pass, while SAQ P2PE, SPoc, B and B-IP see no change in their training requirements.
Most importantly, organisations that must report under SAQ D, SAQ A-EP or SAC C or C-VT should not wait until the last minute to implement these training changes; training takes time and if the implementation of these changes is left until the last minute, organisations will struggle to show the evidence of effective training that is required if they are to meet compliance deadlines and avoid falling into non-compliance.
Yes, here we go again: Prevention is cheaper than cure
Yes, we’ve harped on about the benefits of preparation, as opposed to the pain and cost of containment and recovery. And we’ll probably do it again, not because we have some special insight, and not because it’s just a PCI DSS issue, but because training is foundational to a successful cyber security-maturity program, as evidenced by plenty of other standards including ISO/IEC 27001:2022 (Control 6.3) and NIST SP 800-53 Rev. 5 (control AT-2).
Training may seem like an inconvenience, but failing to provide it can lead to expensive compliance failures, breach recovery costs, and reputational damage.
PCI DSS compliance is not just a technical issue—it’s an organisational responsibility that requires proper training at every level. The clock stopped ticking back in March 31, 2025, so it’s well past the time to address the human component in your PCI DSS compliance success.
